Recently had to repair a bricked Fiet security camera. If too long of a WPA password is used it will cause a buffer overflow and the camera will crash which results in an endless boot-loop. There doesn’t appear to be a way to recover from this condition without getting serial access or access to the flash memory itself.
Fortunately on the main PCB there are serial connection points. A regular TTY-to-USB converter at 3.3V works. Beware when taking it apart. There is a plastic ring around the PIR sensor that needs to be removed first to get to some screws. It’s just snapped on and I used a spudger to free it. Only the two screws near the main body of the light need to be removed and the PIR sensors can be left in place if you want.


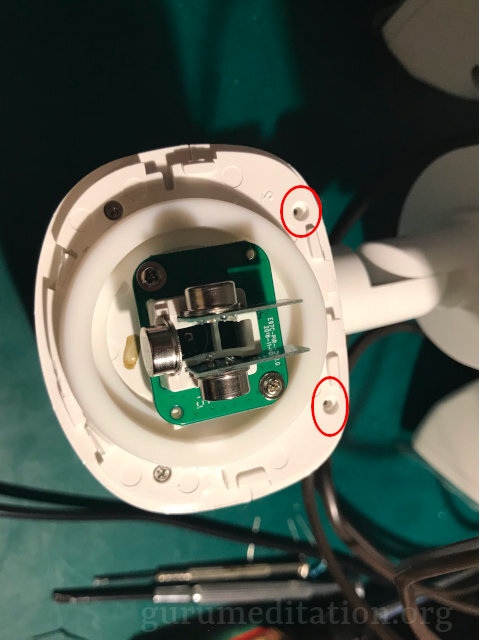
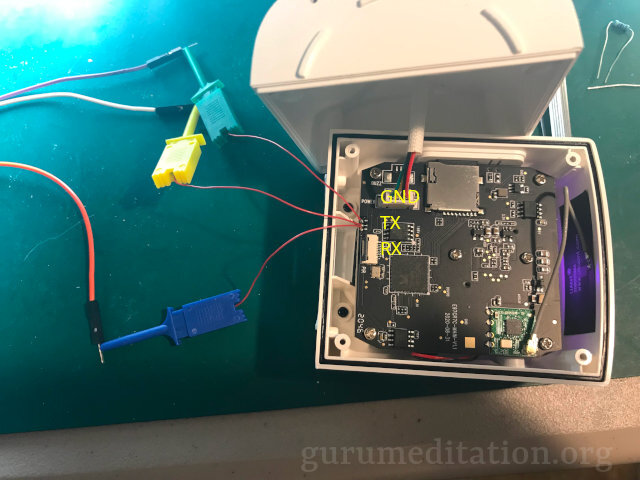
Once you have serial access then the boot process can be stopped to get to the U-Boot menu which will allow you to flash a custom root-fs that has a root password you know.
Warning: r8168#0 failed to set MAC address
set ethaddr = <NULL>
set ipaddr = <NULL>
set netmask = <NULL>
LIN003:Hit any key to stop autoboot:I used the uboot commands to extract the entire flash memory over the serial port (took about 2 hours). This can be done with sf read 80000000 0 1000000 followed by md 80000000 400000. Note the memory display command is real flaky and may hang if you use a size it doesn’t like. It also displays hex with the endianess reversed so every 4 bytes have to be flipped around. Then the root-fs can be sliced out and extracted with unsquashfs. The root password can be created with mkpasswd -m md5crypt. Then recreate the squashfs, patch the filesystem binary with rootfs_tool.py, put the binary on the SD card, then use the fatload command to load it in to memory, then write it to flash with sf write.
During boot there is a second option to stop the boot process. Press q then you can log in as root.
mmcblk0: mmc0:59b4 USD00 118 GiB
mmcblk0: p1
If you want to run app by yourself, please input q
=======================Press q -> EntryThe problem lies within the /mnt/mtd/aoni_ipc daemon that runs on the camera. This is a large master binary that handles all sorts of activities. I couldn’t find source code for it so I had to hack the binary itself. The problem lies in the Config_Read_String_Params function. When the WiFi configuration is read it uses two buffers. The first buffer is 300 bytes but the second one is only 68 bytes. The first buffer is copied to the second during processing. The configuration is base64 encoded so a standard 63-character WPA password will overflow the 68-byte buffer and cause a SEGFAULT.
To fix this issue I modified the binary so that WIFI_PWD is not base64 encoded. This way it will fit within the 68-byte buffer and WPA passwords are text anyway. Near the end of the binary is the WIFI_PWD string surrounded by a bunch of nulls. This is the table that determines which parameters are base64 encoded. I simply changed the string to WIFY_PWD so that when the camera checks to see if it needs to do base64 encoding it does not find WIFI_PWD.
002799f0 4e 65 74 00 00 00 00 00 00 00 00 00 00 00 00 00 |Net.............|
00279a00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00279a70 57 49 46 49 5f 50 57 44 00 00 00 00 00 00 00 00 |WIFI_PWD........|
00279a80 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
I also corrected a typo in the latest Feit firmware for the same aoni_ipc binary. It was trying to call ifocnfig instead of ifconfig.
