-
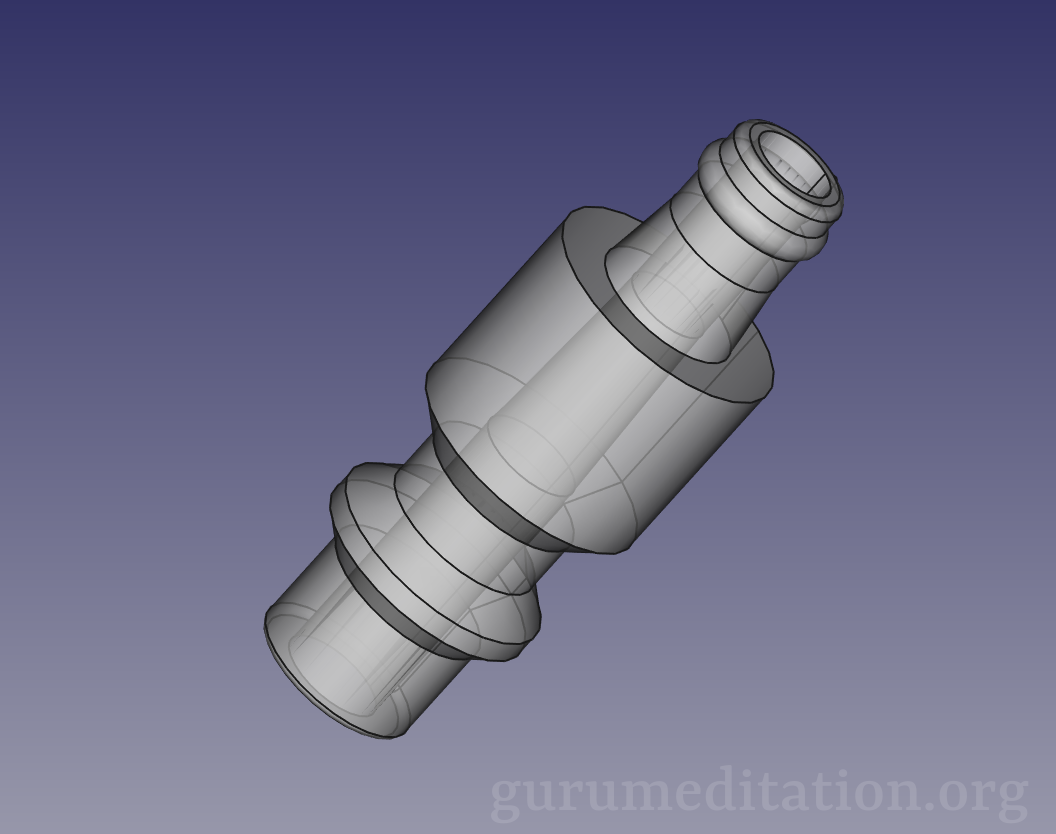
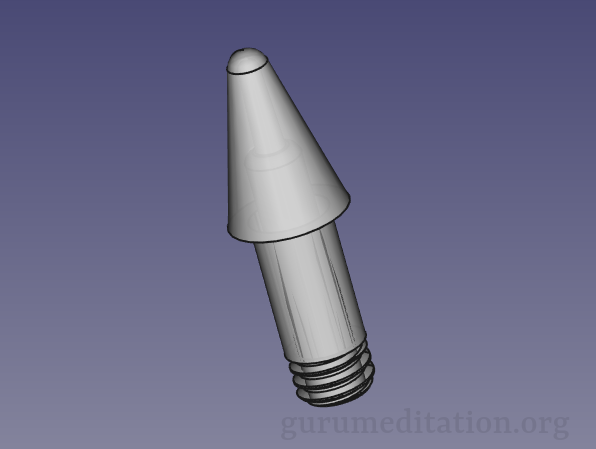
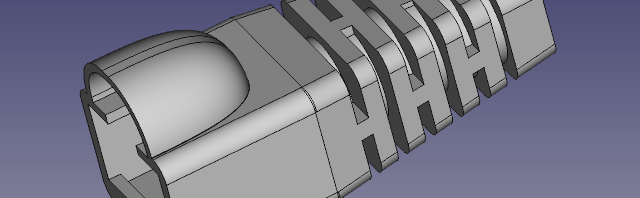
3D printed NPT Industrial to tube couplings
Various fittings to convert 1/4″ NPT Industrial Quick-Disconnect to low-pressure tubes 5/16″ and 3/16″. Both male and female tube fittings are provided. Designed based on official mil-spec MIL-C-4109F and ANSI standard B1.20.1. Shown with Tygon 5/16″ fuel tube (yellow) and 3/16″ aquarium “airline” tubing. I use these to feed air for various low-pressure applications like…
-
3D printed feet for HP 8116A
These are OEM-style rear feet for the HP 8116A function generator. I printed the hole caps in a flexible but the original HP caps are hard plastic. Your choice. I recommend adding a modifier block to change the perimeters or infill to 100% around where the screws clamp down to provide strength. I may create…
-
SD memory card register decoder
This is a utility for decoding SD card registers. On Linux if you have a MMC type card reader (not USB) then you can get the register values with a command similar to: Replace X with the number of your device (use lsblk). That will return the CID and CSD respectively. The CID contains identification…
-
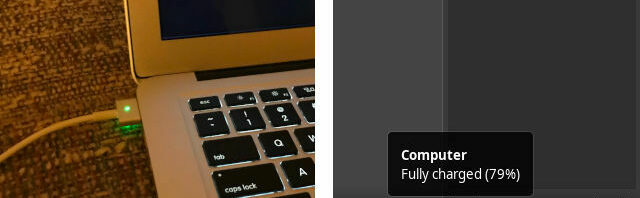
applesmc-next: Battery charge thresholds for Linux on Apple hardware
Update 2025-07-31: Version 0.1.6 with changes to compile on newer kernels. The AUR package has been updated as well. This is a set of patches for the Linux kernel that enable changing the battery charge thresholds. This is useful for example to limit the charge to 80% to prolong the life of your battery if…